Information Gathering, this word is familiar to warriors in cyber security. True? Because there is a saying that “Information is Power”.

Definition of Information Gathering is the process of collecting information about a particular subject from various sources. This can include gathering data about an organization or individual, gathering information about a topic or issue, or gathering data about a system or technology.
There are several types and methods that are familiar when doing Information Gathering, namely Active and Passive.
Active Information Gathering is the process of gathering information by taking direct action, such as sending questions to someone or trying to access a system to gather information about how it works.
Passive Information Gathering is the process of gathering information without taking any direct action or changing anything. For example, gathering information about an organization by reading its website or using a search engine.
Between passive and active information gathering
Passive information gathering refers to gathering as much information as possible without establishing contact between the pen tester (yourself) and the target about which you are collecting information. Active information gathering involves contact between the pen tester and the actual target.
Information Gathering Techniques and methods.
Hackers use a wide variety of techniques and tools to obtain this valuable information about the target, as well as the location or software by collecting data that will be used to achieve the purpose of gathering information….
Let’s take a look at the top information collection methods used to gather information…
How to gather information ?
- Search Engines : Web crawlers can be used to fetch information about anything, and this includes companies, persons, services, and even real hacks, as seen in our previous article about Google Hacking, Shodan, Censys, Zoom Eye, Netcraft, Crt.sh, dll.
- Social Engineerings: This includes in-person chat, phone conversations and email spoofing attacks. What all these methods have in common is the psychology of human weakness, needed to get maximum data about the target.
- Social Media networks: Facebook, Twitter, Instagram, LinkedIn and other social networks are great sources of information to build a profile, especially when targeting individuals.
- Domain names: These are registered by organizations, governments, public and private agencies, and people. Therefore, they’re a great starting point when you want to investigate someone. Personal information, associated domains, projects, services and technologies can be found by inspecting domain name information.
- Internet servers: authoritative DNS servers are a great source of information, as they often include every single surface point exposed to the Internet — which means a direct link to related services such as HTTP, email, etc. In our previous article about passive DNS, we analyzed the importance of DNS servers, and especially passive DNS-recon services, such as the ones we offer here at SecurityTrails.
Some Information Gathering Tools
- Wappalizer
- Netcraft
- DNSenum
- WaybackMachine
- Recon-ng
- Sublis3r
- Netcat
- Nmap
- Whois Lookup
- nslookup
- Google Dorks
- zoomeye
- shodan
- censys
- zoom Eye
In this session, I will try to provide examples of information gathering on 2 vuln webs.
- Try to do Active information gathering on http://testphp.vulnweb.com/ and the results are like this…

Try Active Scanning using Nmap Tool used command “sudo nmap -sV -A <domain target>”
- -sV: Probe open ports to determine service/version info
- -A: Enable OS detection, version detection, script scanning, and traceroute
and i get results like thiss…
- rDNS record for 44.228.249.3: ec2–44–228–249–3.us-west-2.compute.amazonaws.com
- PORT STATE SERVICE VERSION
80/tcp open http nginx 1.19.0
|_http-title: Home of Acunetix Art - OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:4.0
Aggressive OS guesses: Linux 2.6.18–2.6.22 (86%), Linux 4.0 (85%) - Network Distance: 22 hops
- TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1. 0.96 ms 192.168.0.1
2. 12.13 ms 10.134.0.1
3. 13.00 ms 140.213.50.231
4. 21.76 ms 1.9.241.226
5. 40.63 ms 1.9.241.225
6. 207.49 ms if-ae-45–2.tcore2.svw-singapore.as6453.net (180.87.15.248)
7. 201.70 ms equinix02-sfo5.amazon.com (206.223.116.236)
8. 203.61 ms 52.93.70.186
9. 200.89 ms 54.240.242.39
10 …
11. 199.38 ms 64.86.197.113
12 … 18
19. 224.31 ms 108.166.228.39
20 … 21
22. 219.92 ms ec2–44–228–249–3.us-west-2.compute.amazonaws.com (44.228.249.3)

I tried to open the view page source and get access to login to the website.
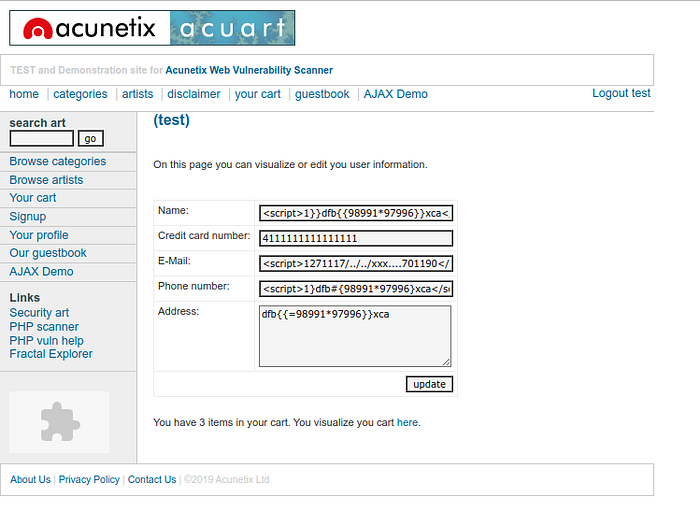

and try to add a ‘ in the url



and i get response Warning about mysql_fetch_array(), and we get information about the database used (Mysql). this web is potential SQL Injection.
Try Getting information using Nikto :
try to scanning this website using Tool Nikto, i get some information about like thiss.
- Target IP: 44.228.249.3
- Target Hostname: testphp.vulnweb.com
- Target Port: 80
- Server: nginx/1.19.0
- Retrieved x-powered-by header: PHP/5.6.40–38+ubuntu20.04.1+deb.sury.org+1
- The anti-clickjacking X-Frame-Options header is not present.
- The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type.
What is Clickjacking ?
Simply put, clickjacking is a malicious act committed by a hacker or a group of hackers by tricking users into clicking on a button or link. It becomes dangerous because the hacker will embed a script or code, where the script can steal data or control the computer of the user who clicks on the link or button.
using whatweb tool to recon.
used command “whatweb testphp.vulnweb.com — verbose”
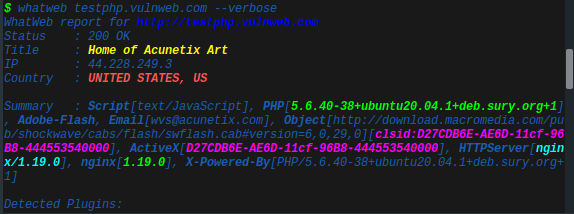
- — verbose : Verbose output includes plugin descriptions.
there is a lot of information that can be obtained
Summary :
- Script[text/JavaScript]
- PHP[5.6.40–38+ubuntu20.04.1+deb.sury.org+1]
- Adobe-Flash
- Email [wvs@acunetix.com]
- Object[http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=6,0,29,0]
- [clsid:D27CDB6E-AE6D-11cf-96B8–444553540000]
- ActiveX[D27CDB6E-AE6D-11cf-96B8–444553540000]
- HTTPServer[nginx/1.19.0], nginx[1.19.0]
- X-Powered-By[PHP/5.6.40–38+ubuntu20.04.1+deb.sury.org+1]
List Description about Detecting Plugins :
- [ ActiveX ]
ActiveX is a framework based on Microsoft’s Component Object Model (COM) and Object Linking and Embedding (OLE) technologies. ActiveX components officially operate only with Microsoft’s Internet Explorer web browser and the Microsoft Windows operating system. — More info: http://en.wikipedia.org/wiki/ActiveX
Module : D27CDB6E-AE6D-11cf-96B8–444553540000
- [ Adobe-Flash ]
This plugin identifies instances of embedded adobe flash files.
Google Dorks: (1)
Website : https://get.adobe.com/flashplayer/
- [ Email ]
Extract email addresses. Find valid email address and syntactically invalid email addresses from mailto: link tags. We match syntactically invalid links containing mailto: to catch anti-spam email addresses, eg. bob at gmail.com. This uses the simplified email regular expression from http://www.regular-expressions.info/email.html for valid email address matching.
String : wvs@acunetix.com
String : wvs@acunetix.com
- [ HTTPServer ]
HTTP server header string. This plugin also attempts to identify the operating system from the server header.
String : nginx/1.19.0 (from server string)
- [ Object ]
HTML object tag. This can be audio, video, Flash, ActiveX, Python, etc. More info:
http://www.w3schools.com/tags/tag_object.asp
Module : clsid:D27CDB6E-AE6D-11cf-96B8–444553540000 (from classid) String : http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=6,0,29,0
- [ PHP ]
PHP is a widely-used general-purpose scripting language that is especially suited for Web development and can be embedded into HTML. This plugin identifies PHP errors, modules and versions and extracts the local file path and username if present.
Version : 5.6.40–38+ubuntu20.04.1+deb.sury.org+1
Google Dorks: (2)
Website : http://www.php.net/
- [ Script ]
This plugin detects instances of script HTML elements and returns the script language/type.
String : text/JavaScript
- [ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.6.40–38+ubuntu20.04.1+deb.sury.org+1 (from x-powered-by string)
- [ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server.
Version : 1.19.0
Website : http://nginx.net/
- HTTP Headers:
HTTP/1.1 200 OK
Server: nginx/1.19.0
Date: Tue, 20 Dec 2022 03:34:46 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: close
X-Powered-By: PHP/5.6.40–38+ubuntu20.04.1+deb.sury.org+1
Content-Encoding: gzip
2. Try to do Active information gathering on http://rest.vulnweb.com/ and the results are like this..

from this web, we can found some information, namely:
- DOCUMENTATION : ACUNETIX VULNERABLE TEST WEBSITES

List Documentation :
- Technologies : Ubuntu 18, Apache, PHP 7.1, MySQL
- Supported Formats: JSON, XML
- Supported Authentication Types: JSON Web Token, Basic Authentication, OAuth2
- Supported Importable File Formarts: Swagger/OpenAPI, Postman, Fiddler
Used NMAP Tool…

Try Active Scanning using Nmap Tool used command “sudo nmap -sS -Pn <domain target>”
- -sS : TCP SYN/Connect()/ACK/Window/Maimon scans
- -Pn : Treat all hosts as online — skip host discovery
and i get results like thiss…
- rDNS record for 35.81.188.86: ec2–35–81–188–86.us-west-2.compute.amazonaws.com
- Not shown: 998 filtered ports
PORT STATE SERVICE
- 80/tcp open http
- 8080/tcp open http-proxy

3. Try to do Passive information gathering on http://testphp.vulnweb.com/ and the results are like this…




4. Try to do Passive information gathering on http://rest.vulnweb.com/ and the results are like this…




There are many more resources and information in Information Gathering, maybe a little explanation from me, Thanks for All…
